Fuzzing with Zed Attack Proxy
The OWASP Zed Attack Proxy, also known as ZAP, "is an easy to use integrated penetration testing tool for finding vulnerabilities in web applications."
Download, unpack, run "./zap.sh", and away we go attacking my blog search interface:
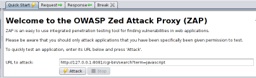
ZAP fuzzes the search parameter. And finds something interesting: "200 OK" is expected, as is "404 Not Found". But "500 Internal Server Error" isn't!

However, Pharo, Zinc and my blog server kept running though, so the 500 wasn't because the server crashed. Indeed, ZAP reports the response thusly:
HTTP/1.0 500 Internal Server Error
Content-Type: text/plain;charset=utf-8
Content-Length: 23
Date: Sat, 08 Jun 2013 14:15:19 GMT
Server: Zinc HTTP Components 1.0
Error: Result Code: 5
Aha! This is an SQLite error: "The database file is locked". Here is one possible StackOverflow explanation. I'll have to verify if that is indeed the cause.
ZAP also offers an SQL injection fuzzer with even more attacks:
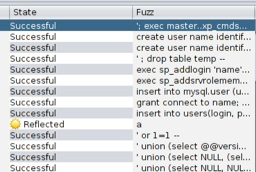
Through all this, the server kept running. Although attacks like "insert into mysql.user (u..." and "exec sp_addlogin 'name'..." returned "Successful", my backend is SQLite and these don't apply.
Still, some time ago while doodling with SQLite, I manage to lock up an image such that it crashes instantly upon re-opening. I haven't found the reason. My conjecture is that it is related to my code's not doing FFI properly, although at this time I have no idea how to test this. I'll probably keep banging on the SQLite interface to see if it eventually kills the image.
Tags: fuzzing, security